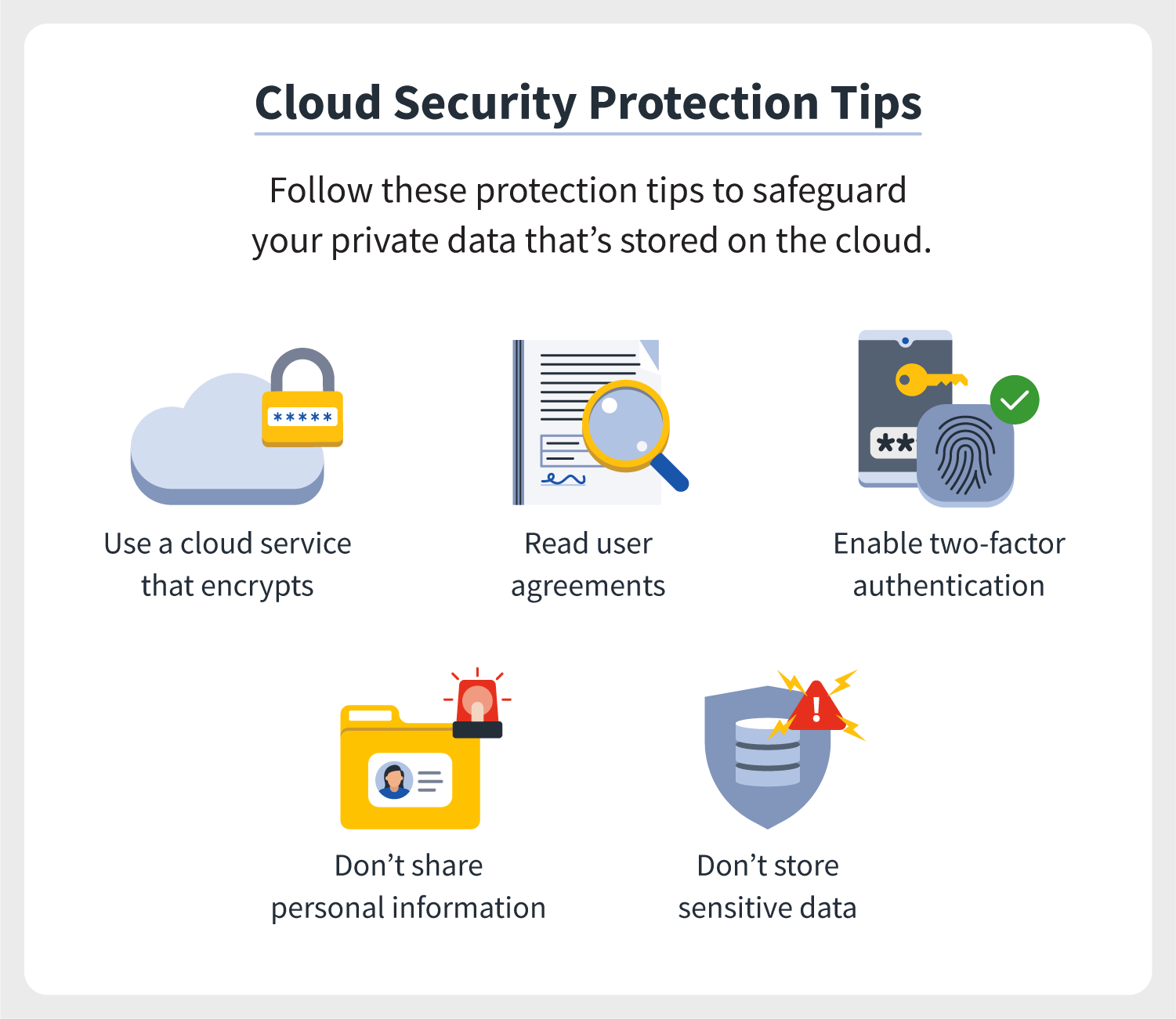
5 Essential Cloud Computing Security Tips
Cloud computing has grown to be an integral part of modern business practices, allowing organizations to access their data and applications from anywhere in the world. This technology offers numerous benefits, including scalability, flexibility, and cost savings. However, the migration to cloud environments also brings with it a host of security challenges. Ensuring data security in the cloud is paramount for any organization that wants to leverage these benefits while minimizing the risks. Here are five essential security tips to safeguard your cloud computing infrastructure:
1. Implement Strong Identity and Access Management (IAM)
Identity and Access Management (IAM) is crucial in the cloud where physical security measures aren’t applicable. Here’s how you can strengthen IAM:
- Use Multi-Factor Authentication (MFA): MFA adds an additional layer of security by requiring users to provide multiple forms of verification before accessing cloud services.
- Role-Based Access Control (RBAC): Ensure access rights are assigned based on job roles, reducing the risk of unauthorized access to sensitive information.
- Regular Audits: Conduct regular audits to track access rights, ensuring that only authorized personnel have access to the necessary resources.
2. Encrypt Data at Rest and in Transit
Data encryption is fundamental to cloud security, protecting your data from unauthorized access:
- Encryption at Rest: Encrypt your data when it is stored within the cloud, using algorithms like AES-256 for robust protection.
- Encryption in Transit: Use protocols like TLS (Transport Layer Security) or SSL (Secure Sockets Layer) to secure data as it travels between your organization and the cloud provider.
🔐 Note: Remember that encryption is only as secure as the keys used. Manage your encryption keys properly, consider using key management services provided by cloud vendors, or opt for a third-party solution for better key management.
3. Secure Configuration Management
Cloud environments are highly configurable, which can be both an advantage and a security risk if not managed correctly:
- Default Configurations: Always change default settings which are often not secure.
- Security Patches: Ensure that your cloud services are up-to-date with the latest security patches.
- Policy Enforcement: Implement and enforce security policies across all cloud resources.
4. Regularly Monitor and Log Activities
Continuous monitoring and logging are essential to detect anomalies:
- Real-Time Monitoring: Deploy tools that provide real-time alerts for suspicious activities.
- Detailed Logging: Keep logs for all access and actions performed within the cloud environment. Logs help in forensic analysis post-incident.
- Intrusion Detection Systems (IDS): Use IDS to detect and respond to security breaches promptly.
5. Implement Data Backups and Disaster Recovery Plans
Data loss can occur due to various reasons including human error, cyberattacks, or system failures. Here are some steps to mitigate these risks:
- Regular Backups: Schedule automatic backups to ensure data is regularly copied to another location.
- Disaster Recovery Plan: Develop and test a disaster recovery plan that includes recovery time objectives (RTOs) and recovery point objectives (RPOs).
- Geographic Redundancy: Store your backups in geographically diverse locations to prevent single-point failures.
📌 Note: While cloud providers offer built-in backup services, consider your specific needs for data retention, compliance, and accessibility before relying solely on these services.
In conclusion, cloud computing security is a multifaceted discipline that requires vigilance and proactive measures. By focusing on IAM, encryption, configuration management, monitoring, and backup strategies, organizations can significantly enhance their cloud security posture. Each of these tips not only mitigates risks but also fosters an environment where businesses can safely leverage the cloud to drive innovation, efficiency, and growth. Remember, security in the cloud is a shared responsibility, with both cloud providers and customers having roles to play. Implementing these strategies ensures that your data remains secure, your operations continue without interruption, and your organization complies with regulatory standards.
What are the common threats in cloud computing?
+Common threats include data breaches, misconfiguration, insecure APIs, insider threats, and inadequate access control leading to unauthorized access.
Can encryption alone protect data in the cloud?
+While encryption is crucial for securing data at rest and in transit, it should be part of a comprehensive security strategy that includes IAM, regular monitoring, and secure configuration management to be truly effective.
How often should cloud security policies be reviewed?
+It’s advisable to review and update cloud security policies at least annually or whenever there are significant changes in technology, business processes, compliance requirements, or security incidents.
Should I use my cloud provider’s IAM or implement my own?
+Cloud providers offer robust IAM services that are generally sufficient for most organizations. However, for very specific or complex needs, or if you require greater control over identity management, you might consider a hybrid approach or a third-party IAM solution.