5 Essential Cloud Security Tips for 2023
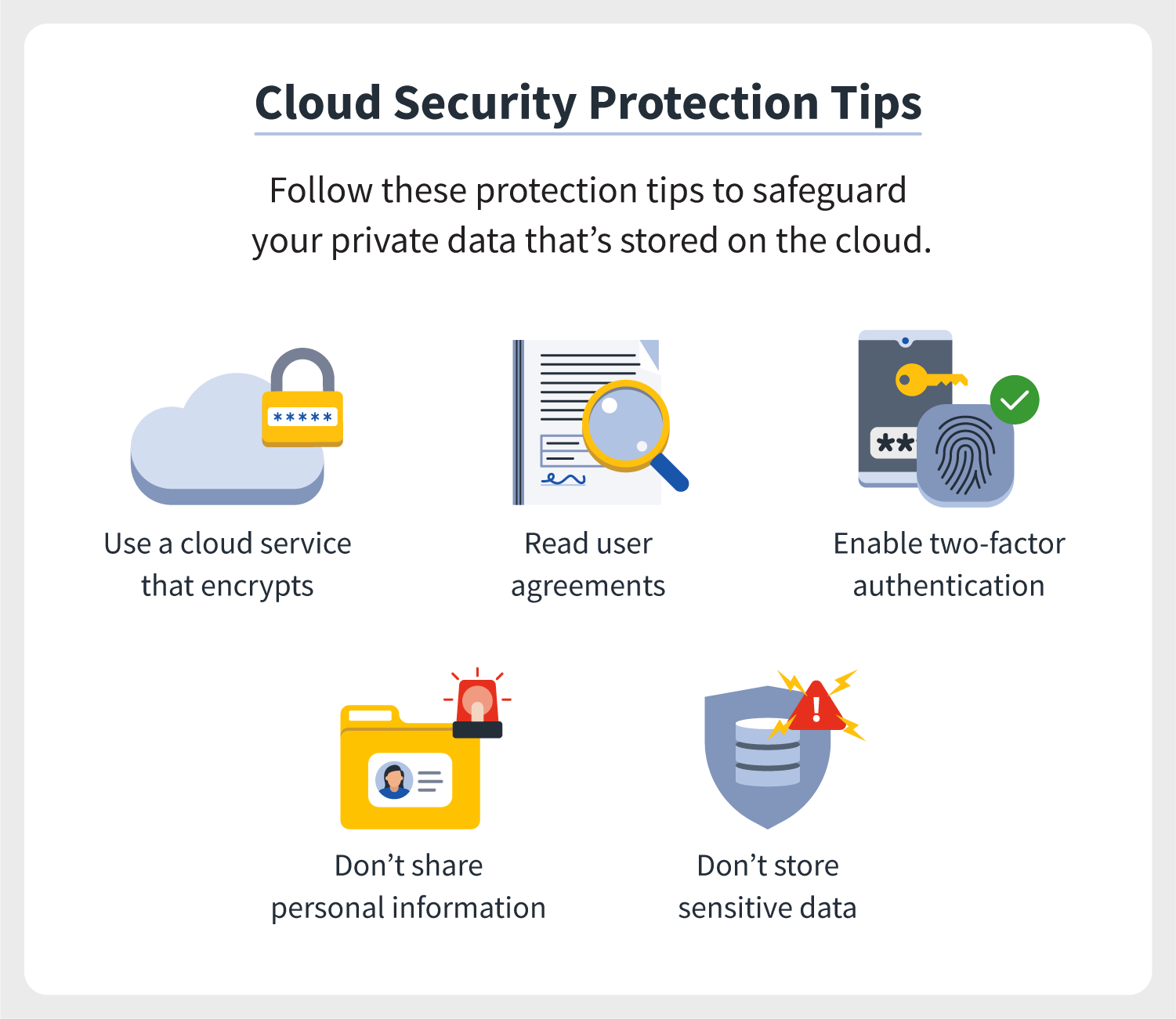
Introduction to Cloud Security
Cloud computing has revolutionized the way businesses operate, offering scalability, flexibility, and significant cost savings. However, with these advantages comes the critical challenge of cloud security. As we delve deeper into 2023, securing your cloud environment has never been more imperative due to the escalating sophistication of cyber threats. This post will guide you through five essential cloud security tips to help safeguard your data, applications, and infrastructure in the cloud.

1. Implement Strong Identity and Access Management (IAM)
Identity and Access Management (IAM) is the cornerstone of cloud security. Here are some steps to fortify this aspect:
- Use Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring more than one method of verification before granting access.
- Regular Audits: Conduct regular audits of access rights. This ensures that permissions align with current employee roles and responsibilities.
- Role-Based Access Control (RBAC): Implement RBAC to provide minimal access rights necessary for each role, reducing the potential impact of compromised accounts.
🔒 Note: Always review and update IAM policies to mitigate insider threats and ensure compliance with regulations like GDPR or HIPAA.
2. Encrypt Data at Rest and in Transit
Encryption is fundamental for protecting data integrity and confidentiality:
- Encryption at Rest: Use AES-256 or equivalent standards for data stored in the cloud.
- Encryption in Transit: Secure your data as it travels across the internet using TLS/SSL protocols.
- Key Management: Control encryption keys with key management services, ensuring you have access to your keys, not just the cloud provider.

3. Utilize Cloud Security Posture Management (CSPM)
Cloud Security Posture Management tools provide:

| Feature | Description |
|---|---|
| Continuous Compliance Monitoring | Ensures your cloud configurations meet regulatory requirements. |
| Vulnerability Management | Detects and alerts on potential security weaknesses. |
| Configuration Drift Detection | Alerts to changes that could weaken security posture. |
🔍 Note: CSPM tools should be integrated with your existing security workflow for real-time monitoring and incident response.
4. Adopt Zero Trust Security Model
The Zero Trust model assumes that threats exist both outside and inside your network:
- Assume Breach: Always verify identity and security context, even for internal users.
- Least Privilege: Grant only the necessary access for users and services to perform their roles.
- Continuous Monitoring: Monitor network traffic, user behavior, and system changes in real time.
- Micro-Segmentation: Isolate workloads to limit lateral movement of threats.

5. Regular Security Training for Employees
The human element remains a significant security vector:
- Phishing Awareness: Train employees to recognize and report phishing attempts.
- Password Management: Educate on creating strong, unique passwords and using password managers.
- Best Practices: Implement security best practices in their daily tasks to reduce risk exposure.
💡 Note: Regularly simulate security scenarios through drills to keep security top of mind for all staff.
By following these essential cloud security tips for 2023, businesses can navigate the complexities of cloud computing with confidence. Ensuring robust IAM, encrypting data both at rest and in transit, using CSPM tools, adopting the Zero Trust security model, and training employees are pivotal steps towards securing your cloud environment. Remember, cloud security is not a one-time task but an ongoing commitment to vigilance and adaptation to evolving threats.
Why is cloud security becoming increasingly important?
+With the proliferation of cyber-attacks and data breaches, cloud security is crucial to protect the vast amount of sensitive data stored in cloud environments.
What is Multi-Factor Authentication (MFA), and why is it important?
+MFA adds an additional layer of security beyond just passwords, significantly reducing the chances of unauthorized access by verifying identity through multiple methods.
How does the Zero Trust model benefit cloud security?
+The Zero Trust model assumes that threats can come from anywhere, even inside the network. It limits access rights, continuously verifies identities, and restricts lateral movement of threats, significantly enhancing cloud security.
Can you explain what CSPM tools do?
+Cloud Security Posture Management (CSPM) tools continuously monitor cloud environments for compliance, configuration weaknesses, and security issues, providing proactive defense and risk management.