Cloud Computing Security: Protecting Your Data in 2023
In today's digital landscape, businesses of all sizes are increasingly relying on cloud computing services for storage, scalability, and flexibility. With this shift comes a crucial responsibility: ensuring the security of your data in the cloud. As we move further into 2023, understanding the nuances of cloud security has never been more critical. Here's a comprehensive guide on how you can protect your data in cloud environments.
Understanding Cloud Security

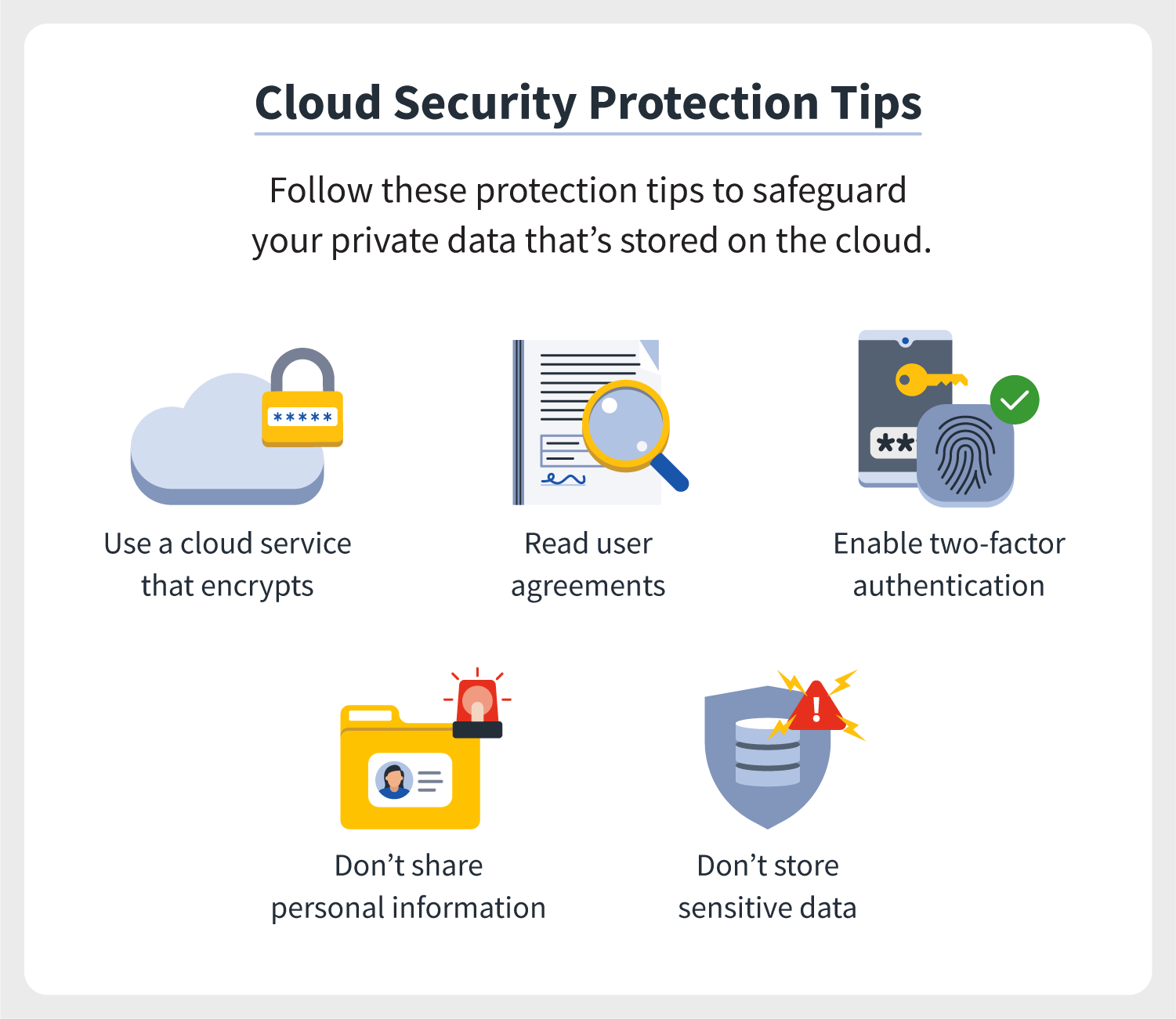
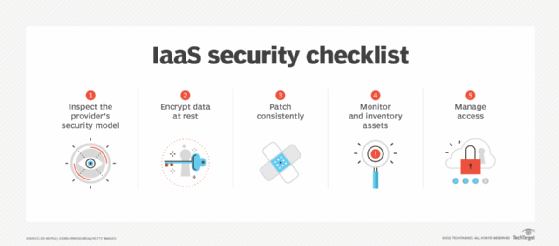
Cloud security refers to a set of policies, controls, procedures, and technologies that work together to protect cloud-based systems, data, and infrastructure from unauthorized access, data breaches, and cyber attacks. Here are key components of cloud security:
- Identity and Access Management (IAM): Ensuring that only authorized users have access to cloud resources.
- Data Encryption: Encrypting data at rest and in transit to prevent unauthorized data access.
- Network Security: Implementing firewalls, secure network configurations, and anti-malware solutions.
- Compliance and Audit: Adhering to industry standards and conducting regular audits.
Security Measures for Cloud Computing
Here are several proactive measures to enhance cloud security:
1. Identity and Access Management
- Multi-Factor Authentication (MFA): Implement MFA to add an additional layer of security, verifying users through multiple methods.
- Least Privilege Principle: Assign permissions based on the minimum level required for a user to perform their duties, reducing potential exposure if credentials are compromised.
- Regular Access Reviews: Conduct regular audits to ensure permissions are still relevant and adjust as necessary.
2. Data Protection
- Encryption: Encrypt data both at rest and during transmission. Use strong encryption standards like AES-256 for data at rest and TLS for data in transit.
- Backup and Recovery: Regularly back up your data and ensure that recovery processes are tested and effective.
- Secure Key Management: Use a robust key management system to control who has access to encryption keys.
3. Network Security
- Firewalls and Intrusion Detection Systems: Deploy firewalls at the perimeter and within cloud networks to block unauthorized access attempts. Use IDS/IPS to detect and respond to threats.
- Virtual Private Networks (VPNs): VPNs can secure access to cloud resources, particularly when connecting from external networks.
- Cloud Security Posture Management: Tools like CSPM help to identify and manage cloud security risks continuously.
4. Compliance and Audits
- Compliance with Regulations: Ensure your cloud setup complies with regulations like GDPR, HIPAA, or PCI-DSS, depending on your industry.
- Regular Audits: Conduct audits to check for compliance, security gaps, and to verify that security policies are being followed.
5. Monitoring and Incident Response
- Continuous Monitoring: Use SIEM (Security Information and Event Management) systems to keep an eye on your cloud environment for suspicious activities.
- Incident Response Plan: Develop a comprehensive plan to quickly identify, respond to, and recover from security breaches.
🔐 Note: Always encrypt your data. Data encryption is your first line of defense against unauthorized access, ensuring that even if data is intercepted or stolen, it remains unintelligible without the decryption keys.
Advanced Threats and Countermeasures
Beyond standard measures, here’s how to address more sophisticated threats:
- Zero Trust Architecture: This security model assumes no one inside or outside the network is trusted, and verification is required for every user or device attempting access.
- Machine Learning for Threat Detection: Implement AI-driven solutions that can learn to detect anomalies in real-time, offering predictive security measures.
- API Security: Many cloud services rely on APIs for interactions. Ensure these are secure against injections, malformed payloads, and unauthorized access attempts.
⚠️ Note: Be vigilant about third-party applications and APIs. They can pose significant security risks if not properly vetted or secured.
Future Trends in Cloud Security
Looking ahead, here are some emerging trends in cloud security:
- Quantum Computing and Encryption: As quantum computing grows, traditional encryption methods could become obsolete, driving the need for quantum-resistant encryption.
- AI and Automation in Security Operations: More organizations will automate security tasks to handle the growing volume of data and threat vectors.
- Serverless Security: As serverless computing gains popularity, securing these environments without traditional servers will become a significant challenge and focus.
🌟 Note: Keeping up with evolving technology trends is key. Constant learning and adaptation are necessary to stay ahead in the realm of cloud security.
In conclusion, securing your data in the cloud in 2023 involves a multi-layered approach that spans across identity management, encryption, network security, compliance, and proactive threat mitigation. By implementing these strategies, organizations can significantly reduce the risk of data breaches and ensure that their cloud environments are resilient against emerging threats. As cloud adoption continues to grow, staying vigilant and informed about best practices in cloud security will be paramount to safeguarding your valuable data.
What is cloud security?
+Cloud security refers to the set of policies, technologies, and controls designed to protect cloud-based systems, data, and infrastructure from unauthorized access, data breaches, and other cyber threats.
Why is encryption crucial for cloud security?
+Encryption is crucial because it turns data into unreadable code unless you have the decryption keys, thereby safeguarding it from unauthorized access even if the data storage or transit is compromised.
How can AI improve cloud security?
+AI can help by learning from historical data to identify unusual behavior patterns or potential threats, enhancing real-time threat detection, and reducing false positives through predictive analysis.
Related Terms:
- Data privacy cloud computing
- future of cloud security
- future of cloud data security
- data loss prevention in cloud
- microsoft cloud data security
- best data security in cloud