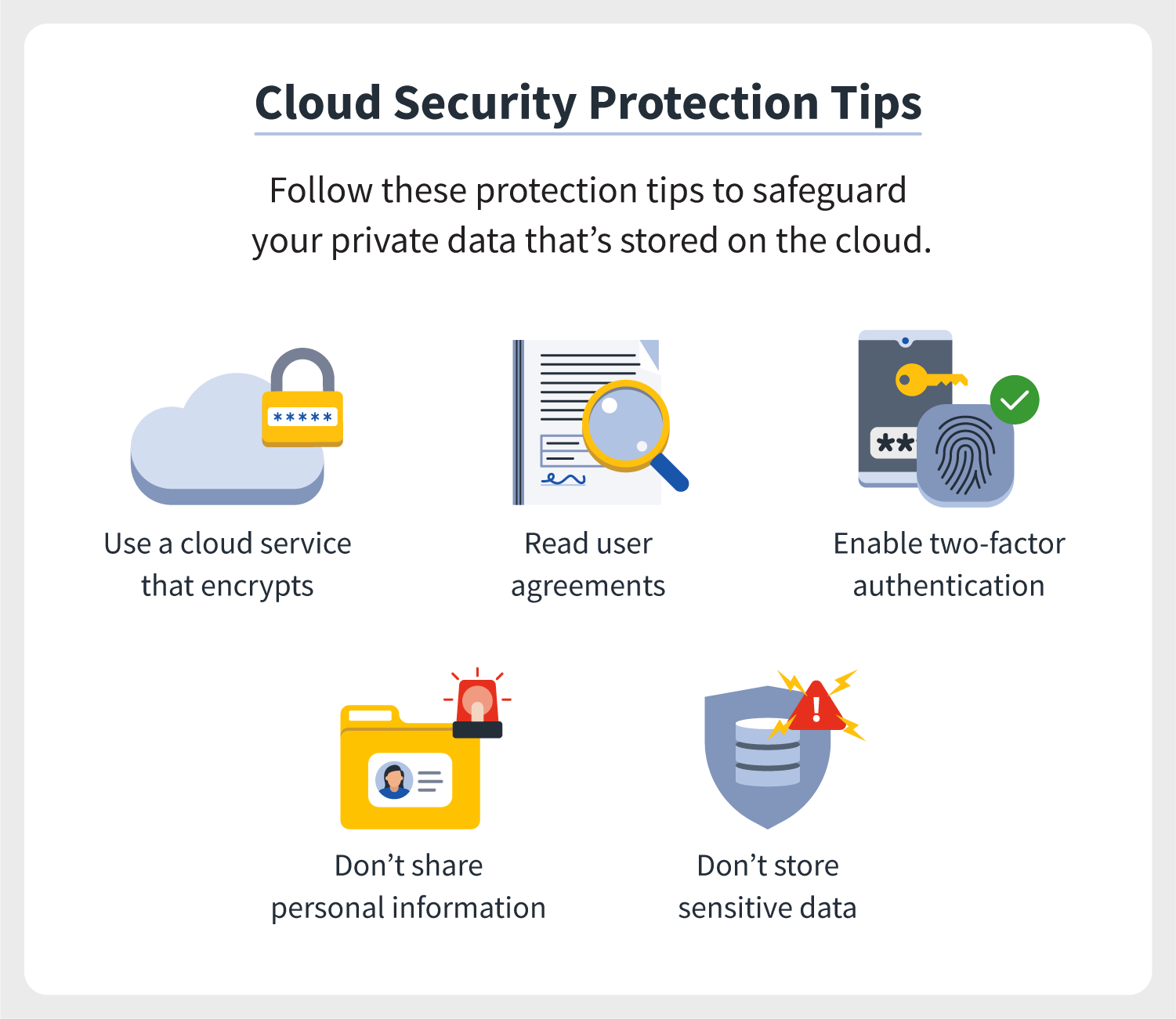
5 Ways to Boost Security in Cloud Computing

As businesses increasingly shift their operations to the cloud, the importance of ensuring robust cloud security has never been greater. From sensitive customer data to critical corporate information, the cloud hosts a treasure trove of valuable assets that, if compromised, could lead to catastrophic outcomes. Here are five proven strategies to bolster your cloud computing security:
1. Utilize Multi-Factor Authentication (MFA)
One of the first lines of defense in securing your cloud environment is the implementation of Multi-Factor Authentication (MFA). MFA goes beyond traditional password protection by requiring additional verification factors, making unauthorized access significantly more difficult.
- Verification through something you know (password),
- Something you have (a security token or smartphone app),
- Something you are (biometrics).
Implementing MFA can dramatically reduce the chances of successful phishing attempts, password compromise, and other cyber threats. Here’s how to do it:
- Set up MFA for all users with access to cloud services.
- Use push notifications to a trusted device or one-time passwords for verification.
- Consider hardware security keys for the most critical accounts.
2. Implement Data Encryption
Data encryption is pivotal in safeguarding your data at rest, in transit, or in use within the cloud. Encrypting data makes it indecipherable to anyone without the key, reducing the impact of a data breach.
- Use encryption algorithms like AES-256 for data at rest.
- Implement Transport Layer Security (TLS) for data in transit.
- Consider application-level encryption for sensitive data fields.
Here’s a basic overview of how you can achieve encryption:

| Encryption Type | Purpose |
|---|---|
| At Rest | Protects data stored on disk. |
| In Transit | Secures data moving over networks. |
| Application-Level | Encrypts specific fields within applications. |
⚠️ Note: Always keep encryption keys separate from your cloud data storage and rotate them regularly to prevent key theft.
3. Regular Security Audits and Penetration Testing
Regularly auditing your cloud environment and conducting penetration tests can help identify vulnerabilities before they are exploited by adversaries.
- Security Audits: Ensure compliance with industry standards like ISO 27001 or SOC 2.
- Penetration Testing: Simulate attack scenarios to test security measures.
4. Identity and Access Management (IAM) Solutions
Effective Identity and Access Management (IAM) ensures that the right users have the right access to resources. Poor IAM practices can lead to accidental or unauthorized data exposure.
- Implement Role-Based Access Control (RBAC) to limit access according to roles.
- Use Just-In-Time (JIT) access for temporary privileges.
- Regularly review and audit access logs to detect any unusual activity.
5. Deploy Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) monitor your cloud environment for malicious activities or policy violations, acting as both a deterrent and a detection tool for cyber threats.
- Network-based IDPS monitors network traffic for suspicious patterns.
- Host-based IDPS looks for suspicious activity on individual devices.
By taking these steps, you enhance your cloud computing security posture, protecting your data and ensuring the integrity of your cloud services. This summary includes critical strategies for safeguarding your cloud infrastructure against common threats.
How often should I perform security audits in my cloud environment?
+Ideally, you should conduct security audits at least quarterly. However, for environments with high levels of data sensitivity or frequent changes, monthly audits or even continuous monitoring might be more appropriate.
Can I use public key infrastructure (PKI) for cloud encryption?
+Yes, PKI can be employed to secure cloud communications through certificates that authenticate users, devices, or services, ensuring that only authorized entities can access encrypted data.
Is it safe to store sensitive data in the cloud?
+Storing sensitive data in the cloud can be safe when appropriate security measures like encryption, access controls, and regular audits are implemented. However, the level of security depends heavily on the robustness of these measures.
Related Terms:
- best practices for cloud computing
- best practices for cloud security
- cloud security best practices 2024
- cyber security in cloud computing