Cloud Computing: Safeguarding Your Data Effectively

The digital era has ushered in a new way of managing, storing, and accessing data through cloud computing. This technology not only offers scalable solutions for storage and computing but also raises important concerns about data security. Understanding how to safeguard your data in the cloud is essential for both businesses and individual users. This comprehensive guide will walk you through the best practices and strategies to ensure your data remains secure in the cloud.
Understanding Cloud Security
Cloud security involves protecting the data, applications, and the infrastructure associated with cloud computing. Here are key elements of cloud security:
- Data Privacy: Ensuring only authorized users can access sensitive data.
- Compliance: Adhering to standards and regulations set by various regulatory bodies.
- Data Protection: Measures to prevent data breaches, data loss, and unauthorized access.
Key Threats in Cloud Computing
The cloud landscape is fraught with various threats:
- Data Breaches
- Insider Threats
- Data Loss
- Account Hijacking
- Insecure APIs
🌐 Note: Threats to cloud security can evolve with new technologies and attack methodologies.
Best Practices for Cloud Security
To mitigate risks, follow these steps:
- Implement Strong Access Control: Use multi-factor authentication (MFA), role-based access control (RBAC), and password policies.
- Data Encryption: Encrypt data at rest and in transit using industry-standard encryption algorithms.
- Regular Audits and Monitoring: Conduct regular security audits and implement real-time monitoring for unusual activities.
- Secure Configuration: Configure cloud services with security in mind, ensuring default configurations are not exploitable.
Securing Data at Rest and in Transit
Encrypting data:
- At Rest: Use server-side encryption where your data is encrypted before storage.
- In Transit: Encrypt data using TLS or SSL during transmission.
🔐 Note: Encryption is a fundamental strategy to protect your data's confidentiality in the cloud.
Choosing the Right Cloud Provider
When selecting a cloud service provider, consider the following:

| Criteria | Importance |
|---|---|
| Security Certifications | Essential |
| Compliance with Regulations | Crucial for industry-specific requirements |
| Data Center Location | Important for data privacy laws |
| Disaster Recovery and Business Continuity | High importance |
Choosing a provider with robust security practices and certifications like ISO 27001, SOC, or FedRAMP ensures that your cloud environment is set up for security.
Backup and Recovery
Even with best practices in place, data loss can occur due to:
- Accidental deletion
- Service outages
- Disaster events
To prepare:
- Regularly back up data to different geographic locations.
- Implement a disaster recovery plan with procedures for data restoration.
- Test recovery processes periodically to ensure data can be recovered in case of an incident.
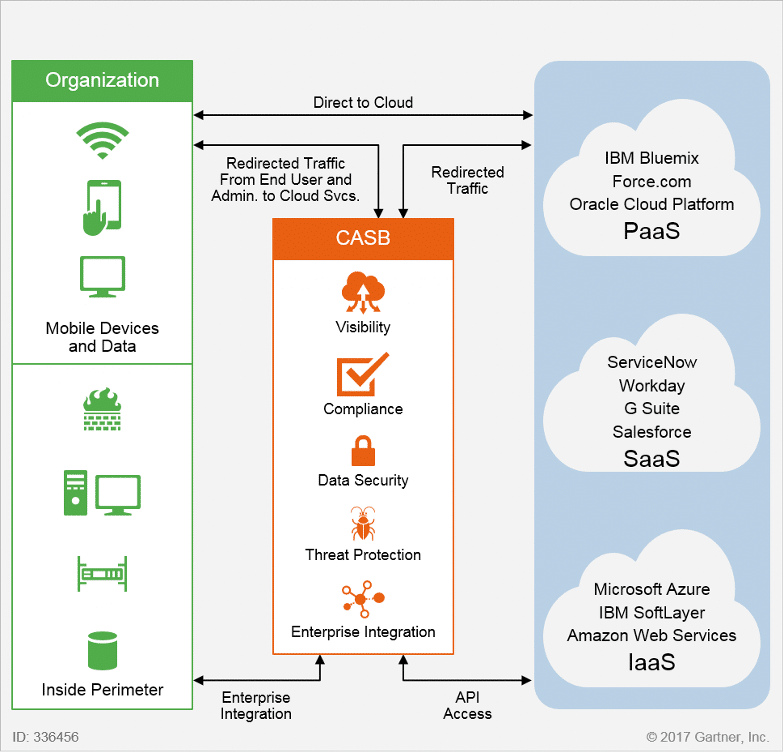
Cloud Access Security Brokers (CASBs)
CASBs act as intermediaries that enforce security policies and ensure compliance:
- Visibility into cloud applications
- Data Loss Prevention (DLP)
- Threat Protection
- Compliance and Governance
🔒 Note: CASBs can significantly enhance your cloud security posture.
In this era where data breaches are not just a possibility but an almost inevitable event, safeguarding your cloud data is paramount. Through the adoption of strong security practices, selecting trusted cloud providers, and staying vigilant, you can ensure your data remains safe. Continuous monitoring, regular updates, and education on cloud security trends will help maintain robust protection against emerging threats.
What are the benefits of cloud security?
+
Cloud security provides several benefits including scalability, flexibility, and cost-effectiveness in securing data. It allows for centralized control over security policies, offers advanced threat detection, and ensures compliance with various regulations.
How often should cloud security audits be conducted?
+
It’s recommended to conduct cloud security audits at least annually or whenever there are significant changes in your cloud infrastructure or business operations.
Can small businesses benefit from cloud security?
+
Yes, cloud security is crucial for small businesses as they are often targeted by cybercriminals due to potentially lower security measures. Cloud solutions offer robust security features that can be scaled according to business needs, providing protection at an affordable cost.
Related Terms:
- data loss prevention in cloud
- cloud data security best practices
- best data security in cloud
- data security in the cloud
- best practices for cloud security
- security in cloud computing