5 Essential Security Tips for Cloud Computing

Cloud computing has become the backbone of modern business operations, offering scalability, flexibility, and cost-efficiency. Yet, with these advantages comes a heightened responsibility for security. As data breaches continue to make headlines, and with cyber threats becoming more sophisticated by the day, understanding and implementing robust security measures in cloud environments is crucial for organizations. Here are five essential security tips for enhancing your cloud computing environment's security posture:
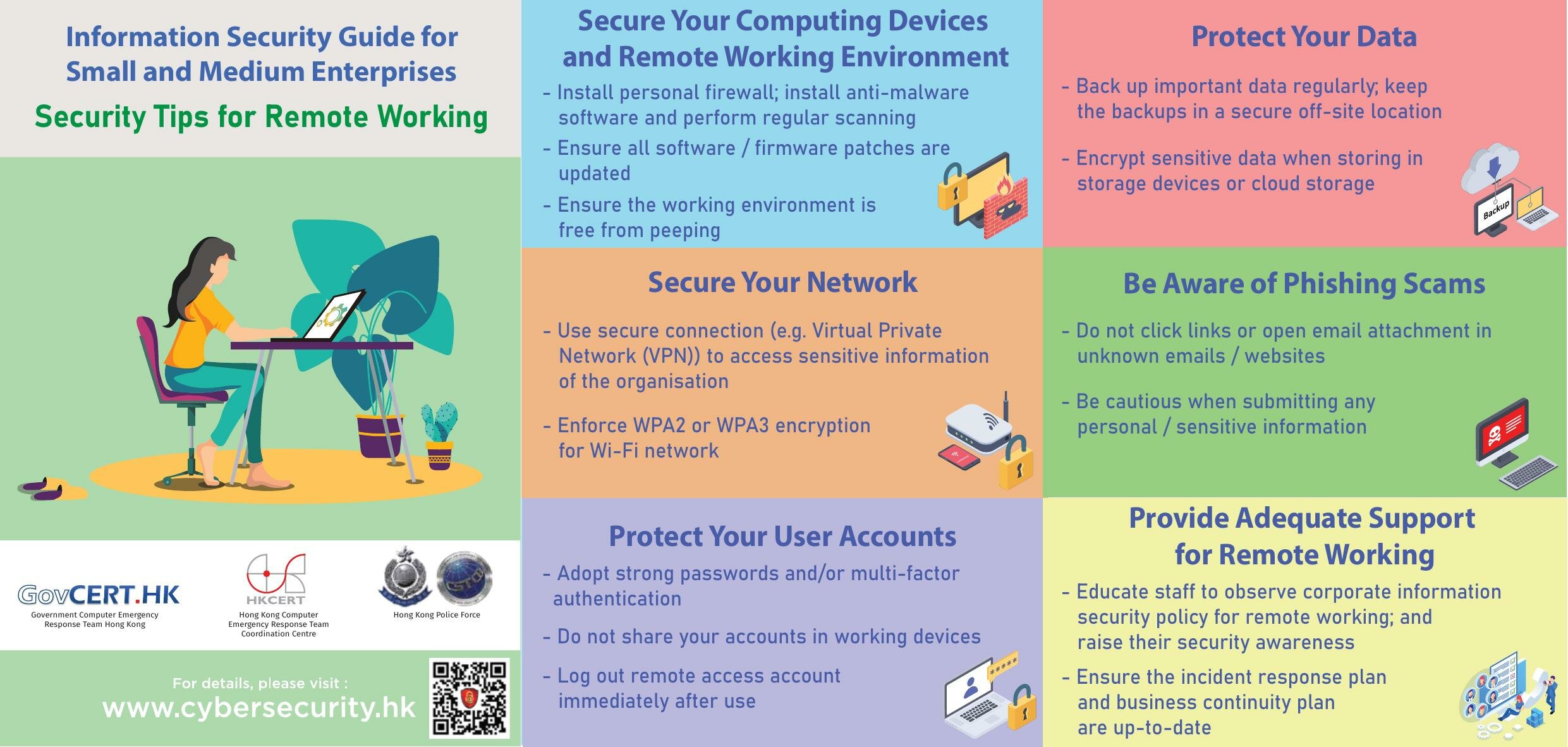
1. Implement Strong Access Controls
The first line of defense in any cloud environment is controlling who can access what. Here are key steps to secure access:
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security beyond just passwords. This can significantly reduce the risk of unauthorized access.
- Identity and Access Management (IAM): Use IAM services to manage permissions and roles effectively. Ensure that users have access only to what they need to perform their roles, following the principle of least privilege.
- Regular Audits: Periodically review access rights to ensure they are current, removing access for employees who have left the company or changed roles.
⚠️ Note: MFA should be mandatory for any sensitive or high-value transactions or accesses.
2. Data Encryption
Encrypting data both at rest and in transit is non-negotiable in cloud environments:
- At Rest: Use encryption standards like AES-256 for data stored in the cloud to prevent unauthorized access even if someone gains physical access to the storage systems.
- In Transit: Implement TLS (Transport Layer Security) to secure data while it moves between your systems and the cloud provider or between cloud services.
🔍 Note: Always use encryption keys managed by you rather than those provided by the cloud service provider for critical data.
3. Regular Security Assessments and Penetration Testing
Assessing your cloud setup's security posture is vital:
- Vulnerability Assessments: Conduct regular scans to identify vulnerabilities in your cloud environment. Tools can help automate this process.
- Penetration Testing: Simulate attacks to find security weaknesses that could be exploited by actual attackers.
The purpose here is to stay one step ahead of potential threats by understanding your environment's weaknesses.
4. Comprehensive Backup and Disaster Recovery Plans
Cloud environments are not immune to disasters:
- Backup Strategy: Implement automated, regular backups with versions of data stored in geographically diverse locations to prevent data loss.
- Disaster Recovery: Have a well-documented disaster recovery plan that includes cloud-specific considerations like reestablishing access, restoring services, and data recovery procedures.
💡 Note: Ensure your backup strategy also protects against logical errors and insider threats, not just physical disasters.
5. Monitoring and Logging
Visibility into your cloud infrastructure is crucial:
- Continuous Monitoring: Use tools to monitor your cloud services for unauthorized activities, anomalies, or suspicious behavior in real-time.
- Logging: Implement comprehensive logging for all activities. Ensure logs are retained for an adequate period for audit and forensic purposes.
- Alerting: Set up automated alerts to notify security teams of potential breaches or unauthorized access attempts.
Regular reviews of these logs and monitoring systems can help in identifying threats early.
Wrapping up, securing cloud computing environments demands a proactive approach. This includes enforcing stringent access controls, ensuring data is encrypted, conducting regular security assessments, having robust backup and disaster recovery plans, and maintaining thorough monitoring and logging practices. By integrating these security practices, organizations can safeguard their assets, maintain compliance, and enhance trust with clients and partners.
How often should I conduct security assessments in my cloud environment?
+It is recommended to perform security assessments at least quarterly or when significant changes are made to the cloud infrastructure.
Can I trust cloud providers to handle encryption for my sensitive data?
+While cloud providers do offer encryption services, managing your encryption keys yourself provides an additional layer of security and control over your data.
What should be my first step in cloud security?
+Implementing strong access controls, particularly through Multi-Factor Authentication (MFA), should be your first step in securing cloud environments.
Related Terms:
- cloud security best practices 2019
- best practices for cloud security
- how to improve cloud security
- cloud security concerns best practices
- how to manage cloud security
- cloud security monitoring best practices