Safeguarding Data: Essentials of Cloud Computing Security

Protecting your data in the cloud has become more crucial than ever as businesses increasingly rely on cloud computing for its scalability, cost-efficiency, and flexibility. However, with these benefits come significant security challenges that require a deep understanding of cloud computing security essentials. In this blog post, we will explore the various aspects of cloud security, providing you with a comprehensive guide to secure your cloud environment effectively.
Understanding Cloud Security Risks
Cloud security isn't just about data protection; it's about securing the entire environment, from the infrastructure to the applications. Here are some common risks associated with cloud computing:
- Data breaches: Compromised user credentials or vulnerabilities in cloud services can lead to unauthorized access to sensitive information.
- Insufficient Identity, Credential, and Access Management (ICAM): Weak authentication mechanisms and overly permissive access controls can expose data to unauthorized users.
- API vulnerabilities: Cloud services often rely on APIs for interaction. If these are not properly secured, they can become entry points for attackers.
- Compliance violations: Cloud deployments might inadvertently violate regulations like GDPR or HIPAA due to misconfigurations or lack of transparency about data handling.
- Insider threats: Employees or third-party vendors with access to the cloud environment might maliciously or accidentally cause data breaches.
Key Security Measures
To mitigate these risks, adopting a multi-faceted approach to cloud security is essential. Here are some key measures:
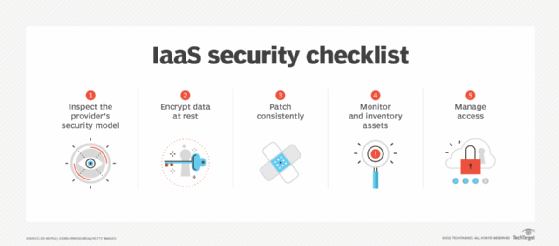
- Identity and Access Management (IAM): Implement strong IAM practices including Multi-Factor Authentication (MFA), least privilege access, and regular audit reviews.
- Data Encryption: Use encryption at rest and in transit to protect data. Cloud providers often offer encryption services, but ensure key management is handled securely.
- Network Security: Implement firewalls, virtual private networks (VPNs), and other network security tools to control access and protect network traffic.
- Vulnerability Management: Regularly scan for and patch vulnerabilities in cloud services and applications.
- Security Information and Event Management (SIEM): Use SIEM tools to monitor, detect, and respond to security incidents in real-time.
🔒 Note: Always ensure that the shared responsibility model is well understood between you and your cloud service provider. This model defines who is responsible for what aspects of security in the cloud.
Implementing Best Practices for Cloud Security
1. Establish Clear Security Policies
Begin by setting up comprehensive security policies. Here's how:
- Define access control policies that detail who can access what data.
- Develop data classification to ensure sensitive data gets the highest protection.
- Create incident response plans to guide actions during a security breach.
2. Secure Configuration Management
Cloud misconfigurations are a common source of security vulnerabilities:
- Utilize automated tools for configuration management to reduce human error.
- Regularly audit your cloud environments to ensure they adhere to security best practices.
- Implement security groups and network ACLs to control traffic flow within your cloud infrastructure.
3. Continuous Monitoring and Auditing
Real-time monitoring and periodic auditing are indispensable:
- Set up monitoring tools to track user activities, system performance, and security events.
- Conduct regular audits of your cloud security posture to identify and mitigate risks.
- Use logging and SIEM systems to provide a clear trail of events for forensic analysis.
👓 Note: Monitoring should not just focus on external threats but also internal activities to catch insider threats.
Advanced Security Techniques
Beyond the basics, consider these advanced techniques to bolster your cloud security:
1. Zero Trust Architecture
Assume breach and verify every request as if it originates from an untrusted source:
- Implement micro-segmentation to isolate workloads and limit lateral movement in case of a breach.
- Use AI and machine learning for adaptive access controls based on behavior analytics.
- Ensure all access decisions are based on real-time context, not just static credentials.
2. Cloud Security Posture Management (CSPM)
CSPM tools help automate security compliance and risk assessment:
- Automate the detection of misconfigurations across cloud services.
- Provide visibility into compliance with industry standards and internal policies.
- Facilitate remediation of vulnerabilities through automated or suggested fixes.
3. Serverless Security
With serverless architectures becoming popular, adapt security practices:
- Implement function-level access controls to reduce exposure of sensitive data.
- Use function signing to ensure only authorized code is executed.
- Integrate security scanning within the CI/CD pipeline to scan for vulnerabilities before deployment.
🖥️ Note: Serverless security must address the unique challenges posed by the event-driven, stateless nature of serverless computing.
Recap of Key Strategies
Throughout this comprehensive exploration of cloud computing security, we've outlined several key strategies to ensure your data remains secure in the cloud:
- Understanding the shared responsibility model between you and your cloud provider.
- Implementing robust Identity and Access Management, encryption, network security, vulnerability management, and real-time monitoring.
- Following best practices such as clear security policies, secure configuration management, and continuous auditing.
- Adopting advanced security techniques like Zero Trust Architecture, CSPM, and serverless security measures.
Ensuring the security of your cloud environment is an ongoing process, requiring vigilance, proactive measures, and a deep understanding of both your cloud infrastructure and the evolving landscape of cyber threats. By prioritizing security and implementing these practices, you can confidently leverage the benefits of cloud computing while minimizing risks.
What is the shared responsibility model in cloud security?
+The shared responsibility model is an approach where the cloud provider is responsible for securing the infrastructure, while you are responsible for securing your data, applications, and endpoints within the cloud environment.
How does encryption at rest and in transit protect cloud data?
+Encryption at rest protects data on disk by encrypting it before storage, making it unreadable without the correct keys. Encryption in transit secures data as it travels across networks, preventing man-in-the-middle attacks by encrypting the transmission.
What are some common signs of an insider threat?
+Unusual login activity, unauthorized access attempts, downloading or transferring large amounts of data, and access to sensitive areas of the cloud without a legitimate need can all be signs of an insider threat.
Related Terms:
- data integrity in cloud computing
- cloud based data protection
- what is cloud security
- cloud data security services
- cloud based security
- cloud data security meaning