Secure Your Cloud: Essential Information Security Tips
As more organizations move towards cloud computing, ensuring the security of cloud data and applications is becoming more crucial than ever. Information security in the cloud involves a wide array of practices and techniques designed to protect your data, privacy, and assets from unauthorized access, misuse, or theft. This blog post will guide you through essential tips and strategies to secure your cloud environment.
Understanding Cloud Security Basics
Before diving into specific security measures, it's important to understand what cloud security entails:
- Confidentiality: Protecting data from unauthorized access.
- Integrity: Ensuring data accuracy and consistency over its entire lifecycle.
- Availability: Ensuring that data and services are available when needed.
- Authentication: Verifying the identity of users or systems accessing cloud services.

Cloud Security Measures
Implement Strong Access Controls
Access controls are the first line of defense in securing your cloud environment:
- Use multi-factor authentication (MFA) to reduce the risk of unauthorized access.
- Set up role-based access control (RBAC) to ensure users have access only to the resources they need.
- Regularly review and adjust access permissions, especially when employees leave the organization or change roles.
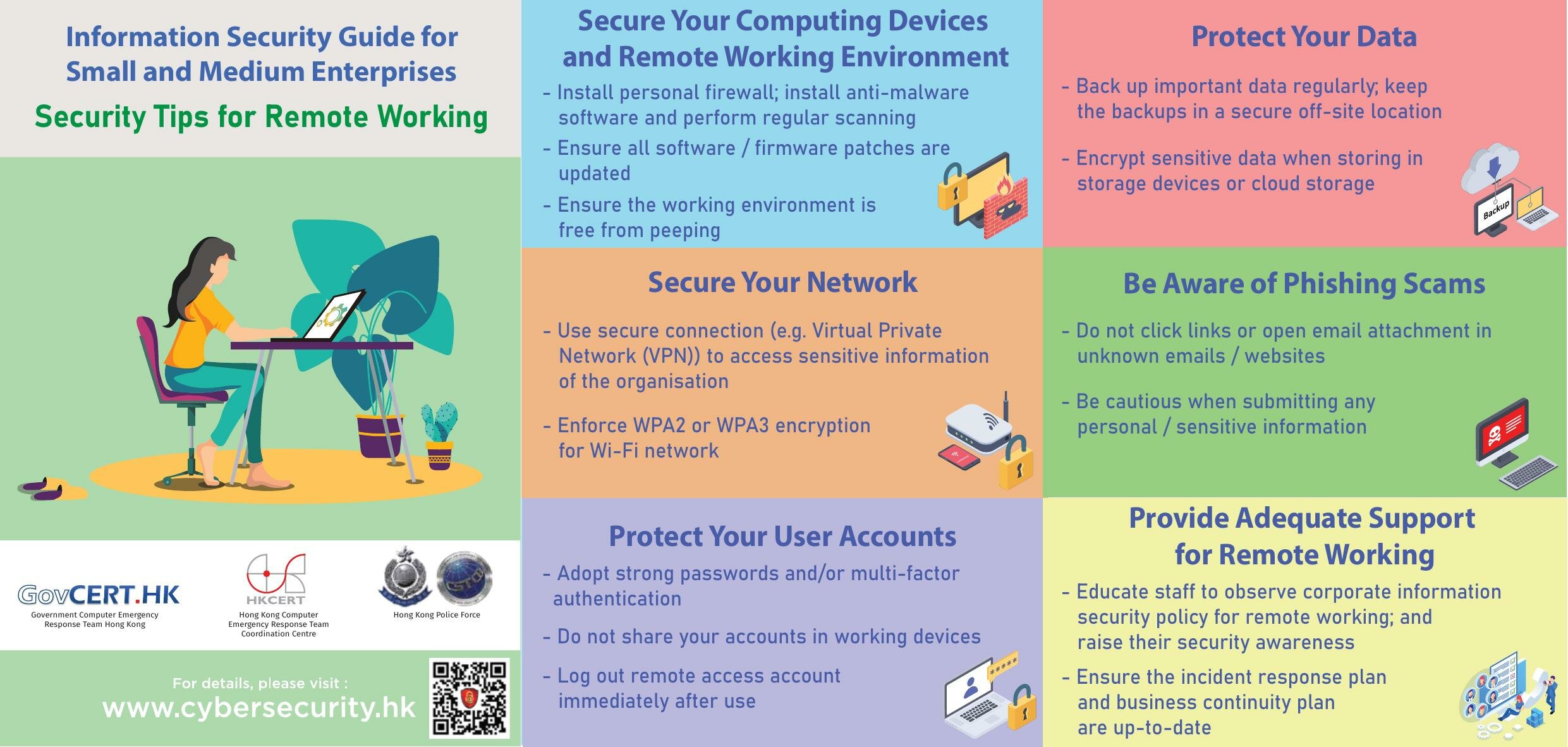
Encrypt Data at Rest and in Transit
Encryption is vital for protecting data:
- Encrypt data at rest with keys that are managed by the organization or a trusted third party.
- Use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) for data in transit.
Secure Network Configuration
Network security is a critical aspect of cloud security:
- Implement a robust Virtual Private Network (VPN) or Direct Connect for accessing cloud services securely.
- Configure firewalls to restrict inbound and outbound traffic based on approved rules.
- Use network segmentation to isolate sensitive data and applications.
Regularly Monitor and Audit
Continuous monitoring helps in identifying and mitigating threats promptly:
- Deploy Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to monitor network traffic.
- Use security information and event management (SIEM) systems to correlate events and detect anomalies.
- Conduct regular security audits to review configurations, access controls, and compliance with standards like ISO 27001 or SOC 2.
Automate Security Processes
Automation can greatly enhance the efficiency of security measures:
- Automate patch management to ensure software and systems are up to date.
- Use tools for continuous configuration audits and compliance checks.
- Implement automated incident response to quickly address breaches or anomalies.
✅ Note: Always ensure that your automation tools are configured to comply with your security policies.
Implement Disaster Recovery and Business Continuity Plans
Cloud services are inherently designed to provide high availability and disaster recovery capabilities:
- Utilize backup and replication options provided by cloud service providers.
- Develop a disaster recovery plan that includes regular testing and updates.
- Ensure your business continuity plan outlines how to recover from data loss or outages.
Advanced Security Measures
Cloud Security Posture Management (CSPM)
CSPM tools help you maintain security and compliance across your cloud infrastructure:
- Continuous assessment of your cloud security posture.
- Detect and address misconfigurations, compliance violations, and vulnerabilities.
Zero Trust Security Model
Adopting a Zero Trust approach means:
- Never assume trust; verify and validate every access request.
- Implement strict identity verification, micro-segmentation, and least privilege access.
DevSecOps Integration
Integrating security into the DevOps pipeline ensures:
- Security checks are automated in the software development lifecycle.
- Security becomes a shared responsibility across all development and operations teams.
By following these tips, organizations can significantly reduce the risk of data breaches, unauthorized access, and other cloud-related security incidents. However, security is not a one-time effort but a continuous process involving vigilant monitoring, adaptation to new threats, and the evolution of security strategies.
The journey towards a secure cloud environment is ongoing. Keeping abreast with the latest security practices, compliance requirements, and evolving threats is crucial. Regular training for employees, reassessment of security policies, and staying informed about cloud provider updates can help maintain a robust security posture.
What is the role of encryption in cloud security?
+
Encryption plays a pivotal role in cloud security by ensuring that data, whether at rest or in transit, remains unreadable to anyone without the appropriate decryption keys. This helps in maintaining confidentiality, protecting against unauthorized access, and ensuring data integrity.
How can I ensure compliance with regulations in the cloud?
+
Compliance in the cloud involves understanding relevant regulations (like GDPR, HIPAA, etc.), leveraging cloud provider’s compliance tools, implementing CSPM for continuous compliance monitoring, and conducting regular audits to ensure adherence to standards.
Can cloud service providers handle all security aspects?
+
While cloud service providers offer robust security measures, security in the cloud is a shared responsibility model. Providers secure the infrastructure, but organizations must secure their data, applications, and configurations. It’s critical for businesses to actively engage in security practices to complement what cloud providers offer.
Related Terms:
- cyber security in the cloud
- best practices for cloud security
- security in cloud computing
- data security in the cloud
- encryption in the cloud
- cloud data security best practices