5 Essential Cybersecurity Tips for Cloud Computing

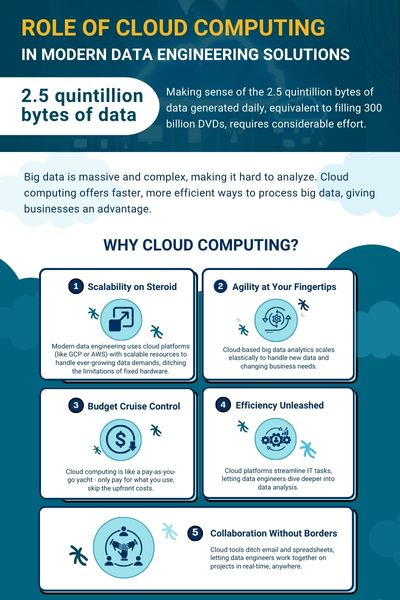
With the increasing reliance on cloud computing, ensuring the security of your data and infrastructure is more crucial than ever. Cloud computing offers many benefits like scalability, flexibility, and cost-efficiency. However, it also introduces unique security challenges. Here are five essential cybersecurity tips to keep your cloud-based systems secure and to minimize the risk of data breaches:
Secure Your Access Points
The first line of defense in any cloud security strategy is to secure the access points to your cloud services. This involves:
- Implementing Multi-Factor Authentication (MFA) for all access.
- Using Strong Encryption for Data in Transit and at Rest.
- Regularly updating Access Credentials and ensuring they are not shared or reused.
🔒 Note: Always enable MFA for cloud access to add an extra layer of security.
Configure Network Security
Proper network configuration can prevent unauthorized access to your cloud resources. Consider the following:
- Setting up firewalls to control incoming and outgoing network traffic.
- Utilizing Virtual Private Clouds (VPCs) to isolate parts of your network.
- Implementing network segmentation to limit lateral movement within the cloud environment.
Monitor and Respond to Threats
Proactive monitoring and quick response to security threats are essential:
- Set up real-time monitoring tools to detect unusual activity.
- Automate alerts for potential security incidents.
- Develop and regularly test an incident response plan.
Enforce Strong Data Management Policies
Data management in the cloud requires a strategic approach:
- Use encryption to protect data both in storage and during transmission.
- Implement data classification to manage and secure sensitive information.
- Regularly backup data to avoid data loss from cyberattacks or hardware failures.
Continuously Train Your Team
Human error remains one of the largest vulnerabilities in cybersecurity:
- Provide continuous cybersecurity training to all employees.
- Conduct phishing simulation exercises to raise awareness.
- Keep your team informed about the latest threats and security best practices.
📚 Note: Cybersecurity training should be an ongoing process, adapting to the evolving threat landscape.
In sum, cybersecurity in cloud computing demands a multi-faceted approach. By securing access points, configuring network security, monitoring for threats, managing data carefully, and training your team, you can significantly reduce the risks associated with cloud environments. Implementing these strategies will help protect your organization's valuable assets and ensure compliance with data protection regulations.
What is Multi-Factor Authentication (MFA)?
+Multi-Factor Authentication (MFA) requires more than one method of verification from independent credential sources to confirm a user’s identity. This could include something you know (a password), something you have (a security token), or something you are (biometric data).
Why is network segmentation important?
+Network segmentation divides a network into smaller, more manageable sections. This limits the spread of malicious activities within the network, making it harder for attackers to compromise the entire system.
How can data classification help with cloud security?
+Data classification categorizes data based on its level of sensitivity. This allows for the implementation of appropriate security measures, ensuring that highly sensitive information is secured with more stringent protocols than less critical data.
What role does encryption play in cloud security?
+Encryption transforms readable data into an encoded version that can only be decoded with the correct key, thereby protecting data from unauthorized access both when it is stored (data at rest) and when it is being transmitted (data in transit).
Can cybersecurity threats be fully eliminated?
+No security measures can guarantee the complete elimination of threats, but by employing best practices and staying vigilant, risks can be minimized to a manageable level, ensuring greater security of your cloud resources.
Related Terms:
- how to improve cloud security