Cloud Computing Security: Safeguarding Your Data in the Cloud

Cloud Computing Security: Safeguarding Your Data in the Cloud is no longer just a buzzword. As businesses and individuals increasingly turn to cloud services for their scalability, flexibility, and cost-effectiveness, the question of how to secure data in these virtual environments has become paramount. Cloud computing security encompasses various practices, technologies, and policies designed to protect data, applications, and infrastructure associated with cloud computing. Here's how you can ensure your data remains safe in the cloud:
Understanding Cloud Security
Cloud security is about creating a secure environment for storing, processing, and transferring data over the internet. Unlike traditional on-premises environments, cloud computing services offer shared infrastructure, which introduces unique security challenges. Here are fundamental concepts to understand:
- Shared Responsibility Model: Both the cloud provider and the user share responsibilities for security.
- Compliance and Certifications: Ensure the cloud provider adheres to industry standards and regulations.
- Data Protection: Implementing encryption, access controls, and regular security audits.
Key Security Measures
To secure your cloud environment, consider implementing these essential security measures:
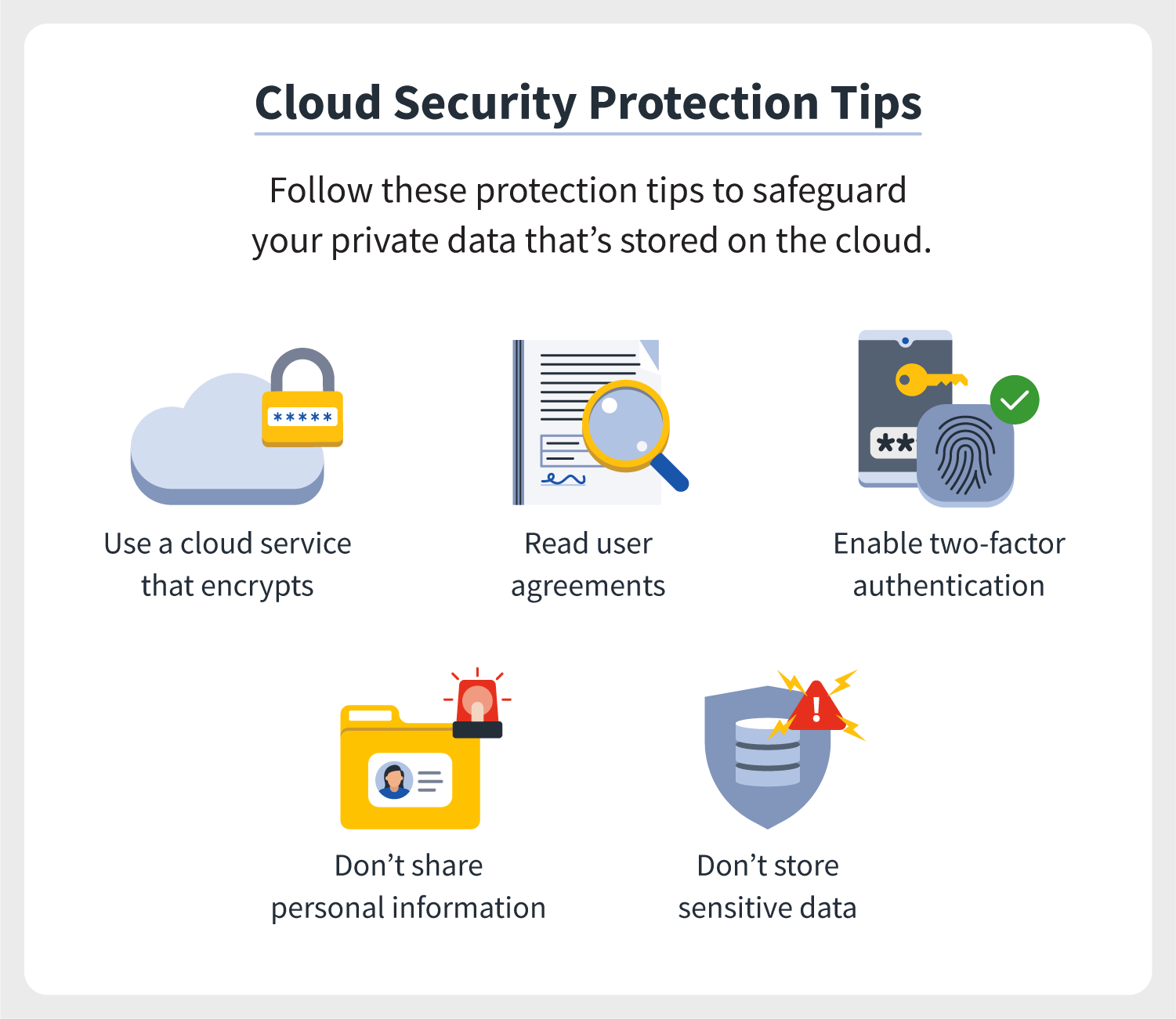
- Encryption: Use encryption at rest and in transit. This means encrypting data before it’s stored in the cloud and ensuring it remains encrypted during transfer.
- Identity and Access Management (IAM): Use strong authentication mechanisms like multi-factor authentication (MFA) and manage permissions carefully to prevent unauthorized access.
- Network Security: Implement firewalls, Virtual Private Networks (VPNs), and intrusion detection systems to safeguard network traffic.
- Data Loss Prevention (DLP): DLP tools monitor and control data transfers to prevent accidental or malicious data leaks.
- Regular Updates: Ensure all software, especially those related to security, are up to date to mitigate vulnerabilities.
Security Best Practices
To enhance your cloud computing security posture:
- Regular Security Audits: Conduct periodic reviews to identify security gaps.
- Use Secure APIs: Ensure all APIs (Application Programming Interfaces) are secure, with authentication and encryption.
- Monitor Activity: Log and monitor all access to your cloud services to detect and respond to suspicious activities.
- Develop an Incident Response Plan: Prepare for how to respond to a security breach with a well-defined plan.
- Educate Your Team: Regular training sessions on cloud security best practices for all employees.
🔑 Note: Cloud security is not a one-time setup but an ongoing process. Constant vigilance and adaptation are key to maintaining a secure cloud environment.
Challenges in Cloud Security
Despite the advantages of cloud computing, several challenges complicate the security landscape:
- Complexity: Managing security across multiple cloud services and ensuring they work in harmony can be complex.
- Data Location: Data might be stored in different countries, each with different regulations on data privacy.
- Insider Threats: Not all threats come from external sources; insiders can pose significant risks.
To address these challenges, consider using:
- Cloud Access Security Brokers (CASBs): These provide visibility, control, and protection for cloud services.
- Secure Configuration Management: Regularly check configurations against known security benchmarks.
- Data Governance: Develop policies for data storage, access, and transfer, respecting international privacy laws.
The Role of Cloud Providers in Security
Cloud service providers like AWS, Google Cloud, and Microsoft Azure play a critical role in cloud security:
- They provide the underlying infrastructure with built-in security features.
- Offer managed security services to offload some security responsibilities.
- Enable customers with various tools for better security management, like identity management and encryption services.
📡 Note: While cloud providers offer robust security features, the user must still configure and manage these features to ensure data security.
The Future of Cloud Security
The evolution of cloud computing security continues as new threats emerge:
- Zero Trust Security Model: This model assumes no one can be trusted and verifies everything before granting access.
- AI and Machine Learning: These technologies are being integrated to predict, detect, and respond to security threats more effectively.
- Cloud Security Posture Management (CSPM): Tools that automate the assessment and management of security posture in cloud environments.
In summary, cloud computing security is a critical aspect of leveraging the cloud's power. By understanding shared responsibilities, employing robust security measures, and staying informed about new threats and technologies, you can safeguard your data. Adopting a proactive approach to cloud security not only protects your data but also instills confidence among your stakeholders, ensuring that cloud computing remains a viable and secure option for modern businesses.
What is the shared responsibility model in cloud computing?
+The shared responsibility model outlines the security responsibilities shared between the cloud service provider and the customer. The provider typically secures the infrastructure, while the customer is responsible for securing data, applications, and possibly the operating system and network traffic within their cloud environment.
How can I ensure my data is secure in the cloud?
+To secure your data in the cloud, implement encryption, use strong IAM practices, adhere to secure network configurations, regularly update and patch systems, and conduct security audits. Also, understanding and leveraging cloud provider security services can significantly enhance your data security.
Are cloud services inherently less secure than on-premises solutions?
+Not necessarily. Cloud services can be very secure if managed properly. They offer economies of scale in security measures that many organizations might not achieve with on-premises solutions. However, the responsibility for security must be shared and managed effectively to ensure the same or even better security than traditional environments.
What are some common threats to cloud security?
+Common threats include data breaches, unauthorized access, misconfigurations, insider threats, and man-in-the-middle attacks. These can be mitigated through proper security practices and vigilant monitoring.
How does AI and Machine Learning play a role in cloud security?
+AI and Machine Learning enhance cloud security by analyzing patterns, predicting potential threats, automating responses to security incidents, and improving anomaly detection. This enables proactive security measures and real-time threat management.
Related Terms:
- Principle of least privilege
- what is multi-factor authentication
- microsoft cloud data security
- security in cloud computing
- cloud based security
- cloud data security services