Top Security Solutions for Cloud Computing in 2023
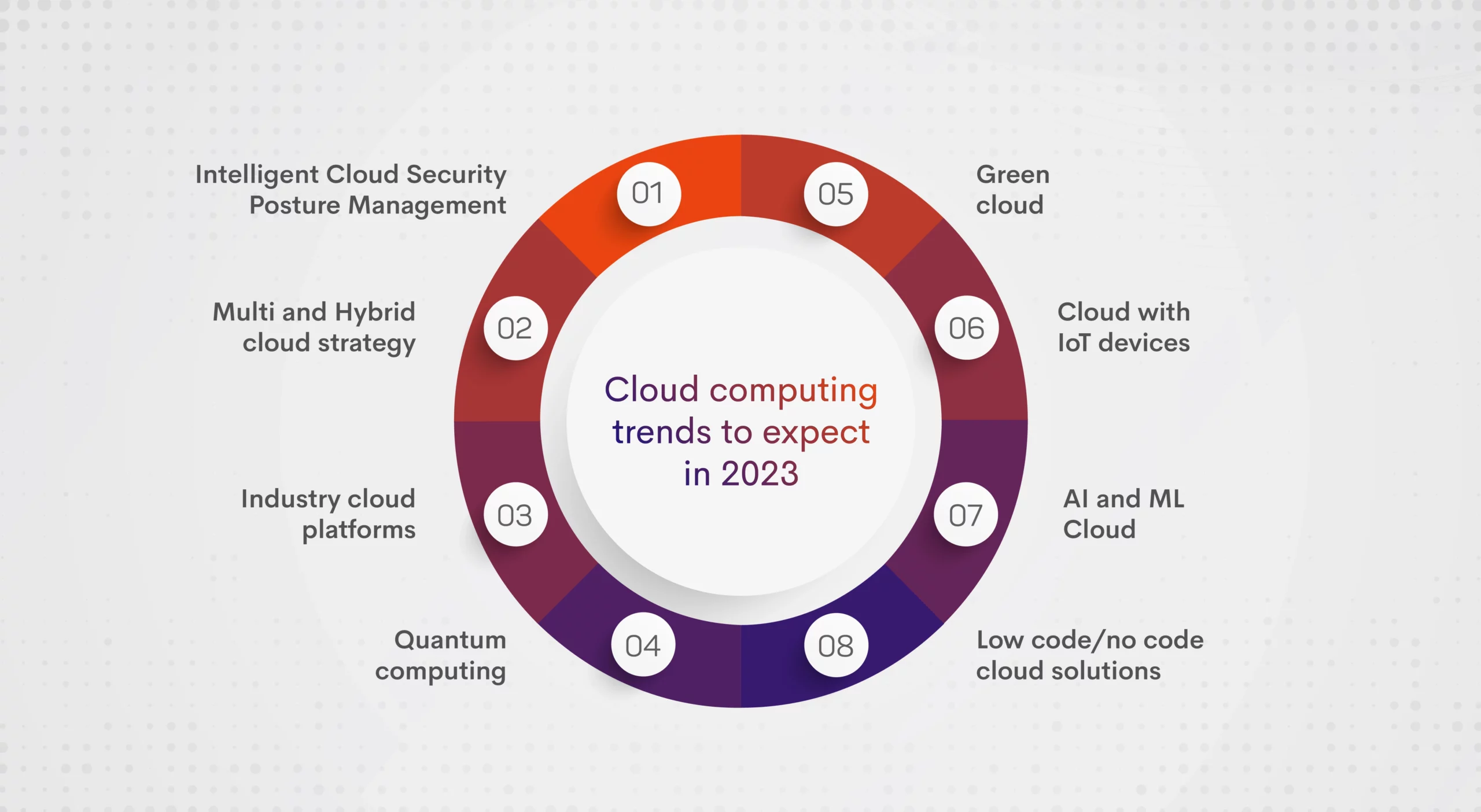
In the era of digital transformation, cloud computing has become the backbone of many businesses, offering unparalleled scalability, flexibility, and cost-effectiveness. However, as companies increasingly move their data and applications to the cloud, ensuring security has become a paramount concern. In 2023, with the evolving threat landscape and advancements in technology, adopting robust security solutions for cloud computing is not just advisable but essential. Here, we will explore the top security measures you can implement to safeguard your cloud environment.
1. Identity and Access Management (IAM)
Identity and Access Management forms the bedrock of cloud security. IAM solutions ensure that only authorized personnel have access to specific resources in the cloud, reducing the risk of unauthorized access and potential breaches. Key components include:
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain access using stolen credentials.
- Role-Based Access Control (RBAC): This approach limits user access rights to the minimum levels needed to perform their job functions, reducing the attack surface.
- Single Sign-On (SSO): SSO enables users to securely authenticate with multiple applications and services with a single set of credentials.
2. Data Encryption
Encrypting data, both at rest and in transit, is critical in securing sensitive information:
- Encryption at Rest: Data stored in the cloud is encrypted, which means even if it’s accessed, it’s unreadable without the key.
- Encryption in Transit: Secure communication protocols like TLS/SSL ensure data safety while moving between the client and the cloud service.
- Key Management: Proper management of encryption keys is crucial, often handled by dedicated Key Management Systems (KMS).
3. Network Security
Securing the network infrastructure is vital for cloud security:
- Virtual Private Cloud (VPC): VPC allows the creation of a logically isolated section of the cloud, providing network level security controls.
- Firewalls and Security Groups: These tools help in filtering unwanted traffic to and from your cloud resources.
- Intrusion Detection and Prevention Systems (IDPS): Monitors network traffic for signs of malicious activities and responds accordingly.
4. Security Information and Event Management (SIEM)
SIEM solutions aggregate log data from various sources to provide real-time analysis of security alerts generated by applications and network hardware:
- Real-Time Monitoring: SIEM tools offer continuous monitoring and analysis to detect suspicious activities.
- Incident Response: These systems help in automated response to security incidents, reducing reaction time.
- Compliance Reporting: Assists in meeting compliance requirements with detailed logging and reporting capabilities.
5. Cloud Access Security Broker (CASB)
CASB acts as an intermediary between users and cloud services to enforce security policies and detect threats:
- Visibility: Provides insights into the usage of cloud services, helping organizations to identify shadow IT.
- Data Security: Offers capabilities like DLP, encryption, and tokenization to protect data shared or stored in the cloud.
- Threat Protection: Detects and mitigates threats like malware, insider threats, and unauthorized access.
⚠️ Note: Remember that the effectiveness of a CASB solution depends heavily on its integration with your existing IT infrastructure.
6. Microsegmentation
Microsegmentation involves dividing the network into smaller, isolated segments to limit lateral movement of threats:
- Granular Security: Control access at an application or workload level, reducing the risk exposure.
- Enhanced Visibility: Understand network traffic flows more intimately to detect and respond to unusual behavior.
- Reduced Attack Surface: By limiting interconnectivity, you significantly decrease the potential impact of an attack.
7. Cloud Security Posture Management (CSPM)
CSPM tools automate the continuous monitoring, detection, and correction of configuration errors:
- Compliance Assessment: Ensures that cloud configurations meet security standards and regulatory compliance.
- Auto Remediation: Automatically corrects misconfigurations to reduce vulnerabilities.
- Risk Mitigation: Identifies potential risks in real-time, allowing for proactive security measures.
As we conclude, it is clear that securing cloud environments in 2023 involves a multifaceted approach. Companies need to integrate various security solutions to cover all aspects of cloud infrastructure security. From IAM to microsegmentation and CSPM, each plays a crucial role in maintaining a robust security posture. Implementing these strategies not only protects your data and applications but also builds trust with customers and partners by demonstrating a commitment to data protection.
What is the importance of encryption in cloud computing?
+Encryption is vital in cloud computing as it prevents unauthorized access to data by rendering it unreadable to anyone who doesn’t have the proper decryption keys. This includes data both stored in the cloud (at rest) and data being transmitted over networks (in transit), ensuring privacy and integrity.
How does microsegmentation enhance cloud security?
+Microsegmentation reduces the attack surface by segmenting a network into smaller zones, each with its own security policies. This limits lateral movement within the cloud environment, thereby isolating potential breaches and reducing the risk of widespread compromise.
Can you explain how a Cloud Access Security Broker (CASB) works?
+A CASB provides visibility into cloud application usage, enforces security policies, and detects threats. It acts as a gatekeeper for cloud data access, ensuring compliance with company policies and mitigating risks associated with cloud services through functionalities like DLP, encryption, and malware detection.
Related Terms:
- holger schulze cyber security
- future of cloud data security