5 Essential Cloud Computing Security Solutions for 2023
In today's digitally interconnected landscape, cloud computing has become indispensable for businesses aiming to enhance scalability, operational efficiency, and reduce costs. However, as organizations shift more of their operations to the cloud, security concerns become paramount. In this article, we'll explore five essential cloud security solutions that should be on every business's radar in 2023 to safeguard their data and applications in the cloud.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is the cornerstone of cloud security. IAM systems help in managing user identities and permissions securely. Here’s how IAM contributes to cloud security:
- Single Sign-On (SSO): Reduces the need for multiple passwords and streamlines user access to multiple cloud services.
- Multi-factor Authentication (MFA): Adds layers of security, ensuring that only authorized users can access cloud resources.
- Role-based Access Control (RBAC): Limits user access to the minimum necessary for their role, reducing the attack surface.
Implementing an effective IAM strategy can significantly mitigate risks related to unauthorized access and insider threats.
Data Encryption
Data encryption remains a critical security measure in cloud computing:
- At Rest: Encrypting data stored in cloud storage to protect against breaches.
- In Transit: Securing data as it moves between client devices and cloud services, or between cloud services themselves.
Encryption Types
Here’s a quick comparison:
| Type | Description |
|---|---|
| Symmetric | Uses one key for both encryption and decryption. Faster but less secure if the key is compromised. |
| Asymmetric | Employs a public key for encryption and a private key for decryption, offering higher security. |
🔒 Note: Encryption should be paired with key management solutions to ensure keys are as secure as the data they protect.
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management tools monitor your cloud environments for misconfigurations and compliance violations. They are crucial for:
- Real-time visibility into the security posture of cloud infrastructure.
- Automated remediation of security misconfigurations.
- Compliance with standards like GDPR, HIPAA, and others.
These tools use artificial intelligence and machine learning to identify anomalies and potential breaches, providing a proactive approach to security management.
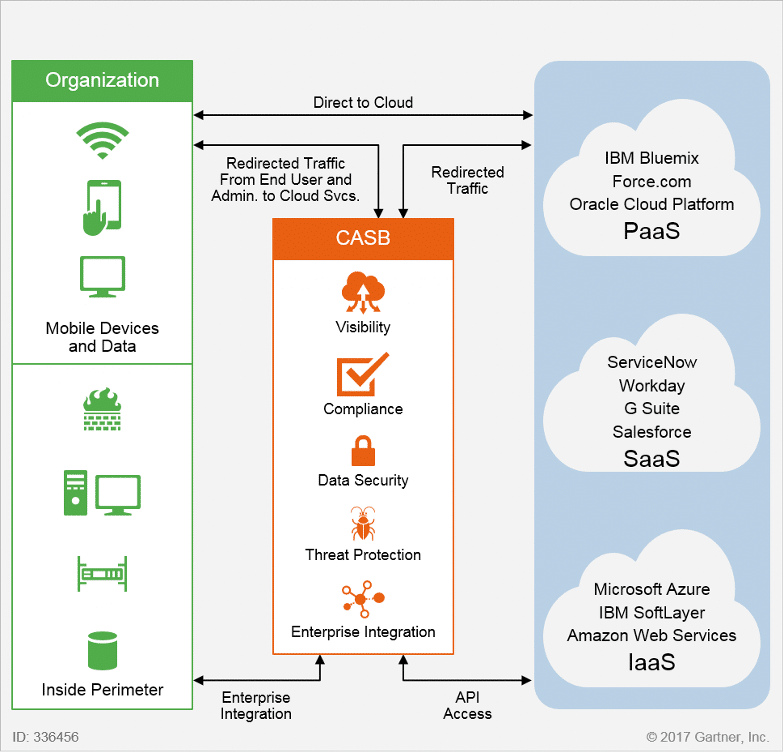
Cloud Access Security Brokers (CASB)
CASBs act as intermediaries between users and cloud service providers to enforce security policies and help in:
- Visibility into shadow IT.
- Enforcement of security policies and access controls.
- Protection of sensitive data through data loss prevention (DLP) mechanisms.
They are particularly useful for organizations dealing with multiple cloud services, ensuring consistent security across all platforms.
Endpoint Detection and Response (EDR)
With the rise in remote work and BYOD (Bring Your Own Device) policies, endpoints are increasingly vulnerable:
- EDR solutions detect and respond to threats at the endpoint level before they propagate through the network or into the cloud.
- These tools provide continuous monitoring, threat hunting, and incident response capabilities.
Integrating EDR with your cloud infrastructure allows for a more holistic security approach, bridging the gap between cloud and on-premise environments.
🌍 Note: Combining cloud-based EDR with existing on-premise security solutions creates a unified security framework.
As we've traversed through these five essential cloud security solutions, it's clear that a comprehensive security strategy requires not just one, but a combination of these tools. IAM lays the foundation with robust access control, encryption secures data both at rest and in transit, CSPM ensures the cloud environment remains compliant and secure, CASBs enforce policies across cloud platforms, and EDR focuses on endpoint protection. Integrating these solutions helps businesses to not only comply with regulations but also build resilience against the evolving cybersecurity threats in the cloud computing arena.
Why is cloud security important?
+Cloud security is critical because the shift to cloud computing means traditional security perimeters are no longer effective. Data breaches, unauthorized access, and compliance violations are significant risks in the cloud environment, making robust security solutions essential to protect sensitive information and maintain business continuity.
Can I use these solutions together?
+Absolutely. These solutions complement each other. For example, using IAM with CASB ensures that access controls are enforced uniformly across all cloud services, while integrating EDR with cloud security solutions can provide a seamless protection from the endpoint to the cloud.
What should be my first step towards cloud security?
+Start by assessing your current cloud environment to understand your assets, data flows, and vulnerabilities. Implementing Identity and Access Management (IAM) should be one of your initial steps to ensure only authorized individuals can access cloud resources.
Related Terms:
- future of cloud data security