5 Essential Security Tips for Cloud Computing

In today's digital landscape, cloud computing has become indispensable for businesses seeking to enhance efficiency, scalability, and innovation. However, while the benefits are substantial, so are the security challenges. As more sensitive data migrates to the cloud, the importance of securing these assets escalates. Here are five essential security tips for cloud computing to ensure your data remains protected:
Implement Strong Identity and Access Management (IAM)
Identity and Access Management (IAM) is critical to cloud security. Here’s how to strengthen it:
- Use Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to confirm their identity through multiple methods (e.g., password, text message, or biometric data). This significantly reduces the risk of unauthorized access.
- Least Privilege Principle: Ensure that users have only the minimum access rights necessary to perform their duties. This minimizes the potential damage from compromised accounts.
- Regularly Review Access:
- Perform periodic audits of user permissions to identify and eliminate unnecessary access.
- Automate these reviews where possible to maintain up-to-date security practices.
🔐 Note: Cloud service providers often offer advanced IAM tools that integrate seamlessly with your existing infrastructure, making implementation easier.
Secure Data in Transit and at Rest
Cloud security must extend to data both in transit and at rest:
- Data Encryption: Always encrypt sensitive data. Here’s a simple breakdown:
- Encryption in Transit: Use protocols like TLS (Transport Layer Security) or SSL (Secure Sockets Layer).
- Encryption at Rest: Data should be encrypted before being stored in the cloud using keys managed by you or a secure key management service.
Implementing encryption ensures that even if data is intercepted or accessed, it remains unreadable without the proper decryption keys.
Regularly Update and Patch Systems
Cloud environments are no less susceptible to vulnerabilities than on-premises infrastructure. Key practices include:
- Automating Security Updates:
- Ensure all cloud services are set to automatically install security patches.
- Configure your cloud provider’s settings to enable patch management systems.
- Monitoring and Responding:
- Subscribe to security alerts from your cloud service provider and relevant software vendors.
- Establish a policy for emergency patching for critical vulnerabilities.
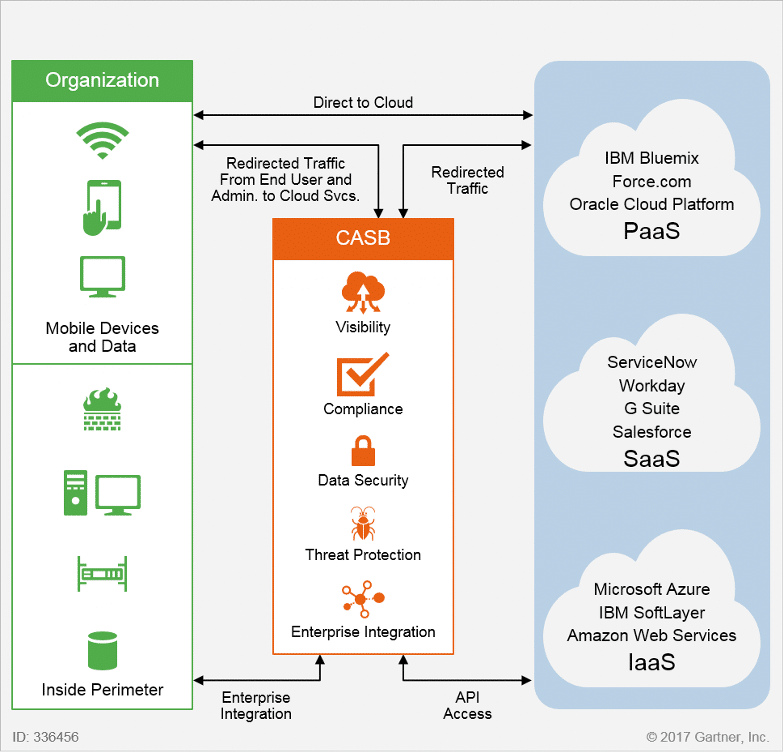
Use Network Security Measures
Here are some effective ways to safeguard your cloud network:
| Security Measure | Description |
|---|---|
| Virtual Private Cloud (VPC) | Create a private, isolated section of the cloud where your instances run, accessible only by your specified IP ranges or through VPN. |
| Security Groups and Network ACLs | Configure security groups to control inbound and outbound traffic for instances, and use Network ACLs as an additional layer of security at the subnet level. |
| DDoS Protection | Employ services like AWS Shield or Cloudflare to mitigate distributed denial-of-service attacks. |
🛡️ Note: Network security in the cloud can often be more scalable and customizable than in traditional environments, offering opportunities for strong defense-in-depth strategies.
Continual Monitoring and Logging
Cloud environments are dynamic, making continual monitoring essential:
- Activity Monitoring: Use tools like AWS CloudTrail or Azure Monitor to log, monitor, and alert on activities that could indicate security breaches or policy violations.
- Real-Time Alerts: Configure automated alerts for unusual or suspicious activity to enable rapid response.
- Log Retention and Analysis: Ensure logs are retained for compliance and forensic analysis. Regularly analyze these logs for patterns or anomalies.
Incorporating these practices not only helps in maintaining a secure cloud environment but also assists in meeting compliance requirements for data protection.
Security in cloud computing is an ongoing process, not a one-time event. The dynamism of cloud environments necessitates continuous vigilance. By implementing these security tips, you can significantly reduce the risk of data breaches and protect your business's integrity. Keep in mind that cloud security is a shared responsibility; while cloud providers secure the infrastructure, you are responsible for securing your data and applications. Being proactive and diligent in applying these security measures will help safeguard your cloud operations effectively.
What is the role of encryption in cloud security?
+Encryption plays a dual role in cloud security by protecting data during transit (while it moves to and from the cloud) and at rest (while it resides on cloud servers). This ensures that even if data is intercepted or accessed without authorization, it remains indecipherable without the appropriate decryption keys, thereby securing sensitive information against unauthorized access.
Why is multi-factor authentication important in cloud security?
+Multi-factor authentication (MFA) adds an extra layer of security beyond just a username and password, requiring users to confirm their identity through multiple methods. This significantly reduces the risk of unauthorized access by ensuring that even if credentials are compromised, access can be blocked without the secondary authentication factor.
How often should cloud security patches be applied?
+Cloud security patches should be applied as soon as they become available, ideally through automated updates. Critical patches that address significant vulnerabilities should be deployed immediately to minimize exposure to potential threats.
What are security groups in cloud computing?
+Security groups act as virtual firewalls for instances, controlling inbound and outbound traffic at the instance level. They are used to define which traffic can reach your instances, thereby enhancing security by only allowing necessary communication.
Is cloud security the responsibility of the cloud provider or the user?
+Cloud security is a shared responsibility. While cloud providers secure the infrastructure, users are responsible for securing their data, applications, access controls, and configuring security settings correctly to ensure overall system security.
Related Terms:
- cloud security best practices 2019
- best practices for cloud security
- how to improve cloud security
- cloud security concerns best practices
- how to manage cloud security
- cloud security monitoring best practices