-

5 Essential Tips for Cloud Security in 2023
Here is a concise and relevant short description for the article titled Cloud Computing Security: Cloud computing security involves protecting data, applications, and infrastructure in cloud environments through various strategies to mitigate risks and unauthorized access. This description covers the essentials: - Keywords: Cloud computing, security - Conciseness: Short and to the point - Focus: Protection measures in a cloud setting - No formatting: Simply plain text
Read More » -

Master Cybersecurity with Cloud Computing: Essential Course
Learn how to secure cloud environments with a comprehensive course on cybersecurity integrated with cloud computing, covering essential tools, techniques, and best practices.
Read More » -
Cloud Computing Software For Small Business
Cloud computing software offers small businesses scalable, cost-effective solutions for data storage, application hosting, and IT management, enabling growth without heavy initial investment.
Read More » -
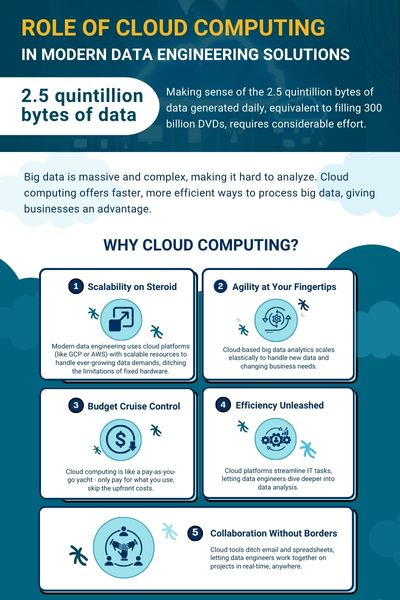
Cloud Computing: Streamline Your Business Processes Effectively
Business process management leverages cloud computing to enhance scalability, reduce costs, and improve efficiency and innovation in process automation.
Read More » -

Cloud Computing Security: Safeguarding Your Data in the Cloud
Cloud computing security focuses on protecting data, applications, and the infrastructure involved in cloud technology, addressing challenges like data breaches, unauthorized access, and compliance with regulations.
Read More » -
Cloud Computing Security: Protecting Your Data in 2023
Cloud computing security addresses the measures, protocols, and practices used to protect cloud infrastructure, data, applications, and services from threats and vulnerabilities. This article explores various security models, risk management strategies, and best practices to ensure robust security in cloud environments.
Read More » -

Secure Cloud Computing: Protecting Your Data Online
Secure cloud computing refers to the practice of protecting data, applications, and infrastructure within cloud environments from various threats, ensuring confidentiality, integrity, and availability.
Read More »