-

Master Cybersecurity with Cloud Computing: Essential Course
Learn how to secure cloud environments with a comprehensive course on cybersecurity integrated with cloud computing, covering essential tools, techniques, and best practices.
Read More » -

5 Ways to Secure Your Cloud Computing Environment
Cloud computing offers scalable, on-demand resources but requires robust security measures to protect sensitive data and ensure privacy and integrity.
Read More » -

5 Essential Cloud Computing Security Tips
Explore robust security measures tailored to protect cloud environments from unauthorized access and cyber threats.
Read More » -

5 Essential Tips for Secure Cloud Computing
Here are essential strategies to safeguard data and infrastructure in cloud computing environments, addressing both common vulnerabilities and advanced security measures.
Read More » -

Essential Security Tips for Cloud Computing Users
Cloud computing security involves protecting data, applications, and infrastructure in cloud environments through measures like encryption, identity and access management, and regular security audits.
Read More » -

Cloud Computing: Safeguarding Your Data Effectively
Cloud computing offers scalable, on-demand resources, but ensuring data security remains a critical challenge. This article explores encryption, access controls, and compliance measures essential for safeguarding data in cloud environments.
Read More » -

5 Essential Security Tips for Cloud Computing
Here's a concise description for the article titled cloud computing and security: Explore the dynamics of cloud computing and the critical security measures needed to protect data and infrastructure in cloud environments.
Read More » -

OVH Cloud Computing: Revolutionizing Your Business Tech Stack
OVHcloud's approach to cloud computing, emphasizing its infrastructure, services, and innovations in the cloud industry.
Read More » -
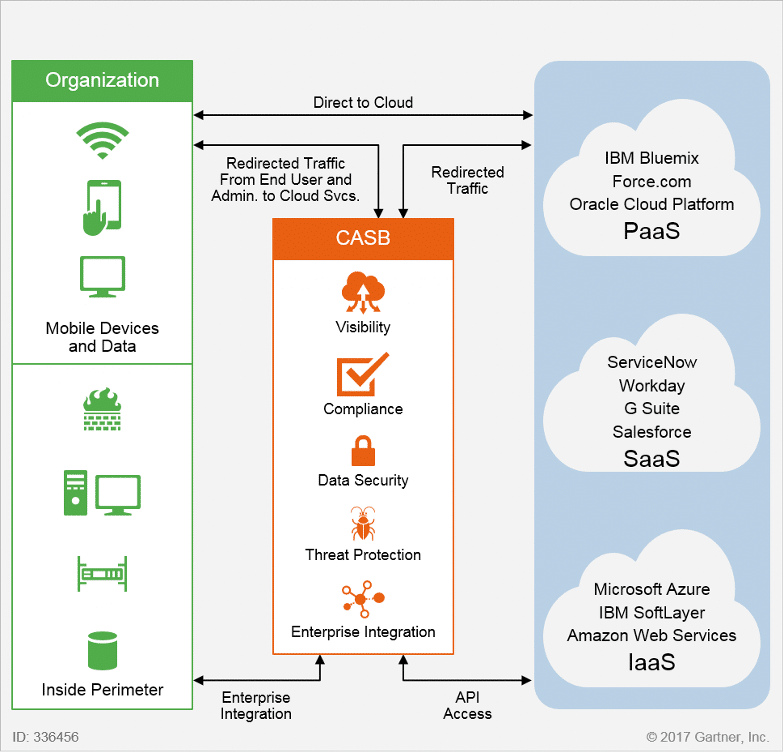
5 Essential Cloud Security Tips for 2023
Cloud computing offers scalable, on-demand resources, but it also brings unique security challenges. This article explores strategies for safeguarding data, applications, and infrastructure in cloud environments.
Read More »