-

Data Security Essentials for Cloud Computing Success
Data security in cloud computing involves protecting information stored, processed, or transmitted through cloud platforms. This encompasses encryption, access controls, compliance, and ensuring data integrity against breaches and unauthorized access.
Read More » -

5 Essential Security Tips for Cloud Computing
Security in cloud computing involves protecting data, applications, and the infrastructure of cloud-based services from cyber threats, ensuring privacy, compliance, and seamless operation.
Read More » -
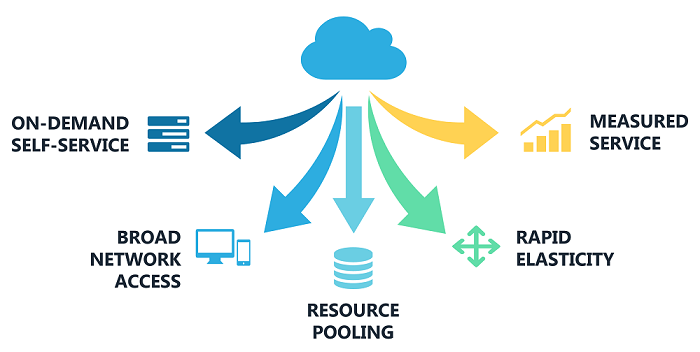
5 Essential Cloud Computing Security Tips
Cloud computing offers scalable resources and services over the internet, but it also introduces significant data security challenges. This article explores the various risks associated with storing and processing data in the cloud and discusses strategies to protect information from breaches and unauthorized access.
Read More » -

Essential Security Tips for Cloud Computing Users
Cloud computing security involves protecting data, applications, and infrastructure in cloud environments through measures like encryption, identity and access management, and regular security audits.
Read More » -

Cloud Computing: Safeguarding Your Data Effectively
Cloud computing offers scalable, on-demand resources, but ensuring data security remains a critical challenge. This article explores encryption, access controls, and compliance measures essential for safeguarding data in cloud environments.
Read More » -

Cloud Computing Network Security Essentials
Ensuring robust network security is paramount in the realm of cloud computing to protect data integrity and confidentiality.
Read More » -
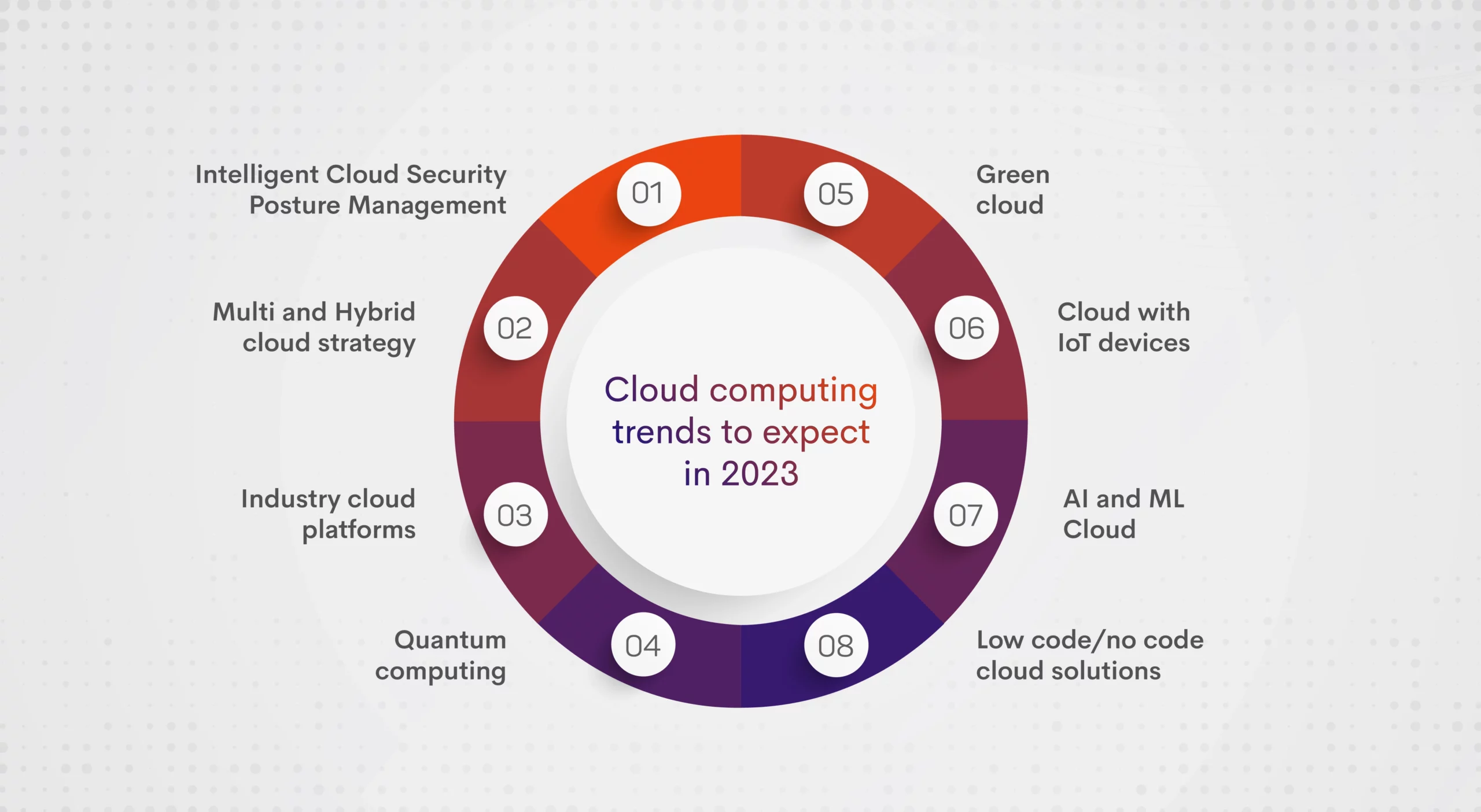
Top Security Solutions for Cloud Computing in 2023
This article discusses various security solutions tailored for cloud computing environments, aiming to protect data, applications, and infrastructure from potential cyber threats.
Read More » -

5 Ways to Boost Security in Cloud Computing
Cloud computing offers scalable, flexible IT resources over the internet but introduces complex security challenges. This article explores key security issues, best practices, and emerging technologies designed to protect data and applications in the cloud environment.
Read More »